Combating Phishing: A Comprehensive Guide for Security Analysts and Employees

Photo by Gadgetvoize on gadgetvoize.com
Hello, a while ago I completed a Mastercard — Cyber Security job simulation on TheForage to tackle phishing email. I completed the tasks and I decided to write a blog on it to learn more on phishing.
TheForage is an online platform that offers free virtual work experience programs created in collaboration with top companies.
Understanding Phishing:
Spam and Phishing are common social engineering attacks where cyber criminals impersonate a trustworthy entity to trick individuals into revealing sensitive information — such as login credentials, financial details, or personal data — or performing actions that compromise security, like clicking malicious links.
In social engineering, phishing attack vectors can be a phone call, a text message, or an email.
History
As widespread and well-known as phishing is now, it hasn’t been around forever. Although the practice originated sometime around the year 1995, coinciding with the rise of the internet and email, these types of scams were not commonly known by everyday people until nearly ten years later. Find more about the phishing history here
Phishing Attacks Techniques
Phishing succeeds by leveraging both psychology and technology. Here are some common techniques:
Spoofing
Faking sender email addresses or phone numbers to appear legitimate (e.g., “support@yourbank.com” might actually come from a malicious domain).
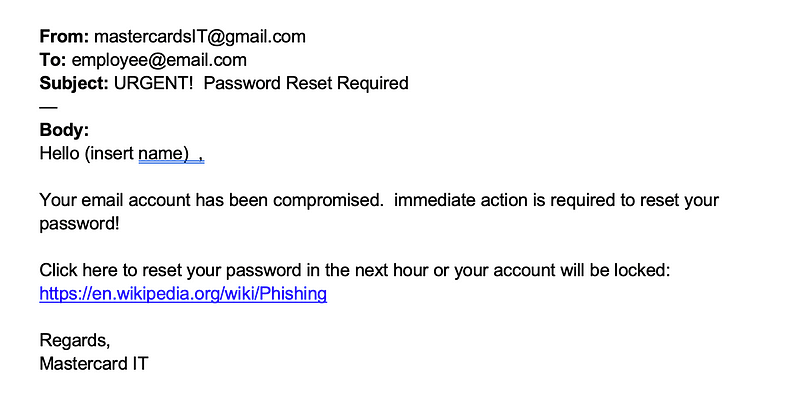
Photo by TheForage on theforage.com
Urgency and Fear
Crafting messages that pressure victims to act quickly (e.g., “Your account will be locked in 24 hours unless you respond”).
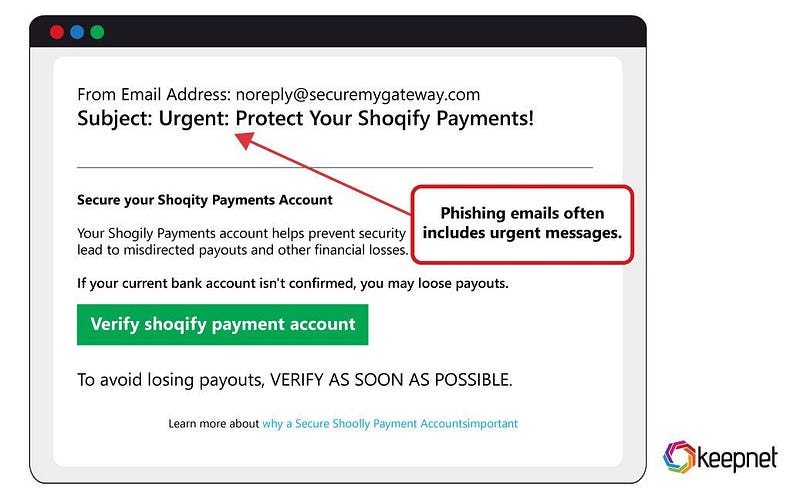
Photo by Keepnet Labs on keepnetlabs.com
Hyperlink Manipulation
Using deceptive URLs (e.g., "www.paypa1.com" instead of "www.paypal.com") or shortened links to hide malicious destinations.
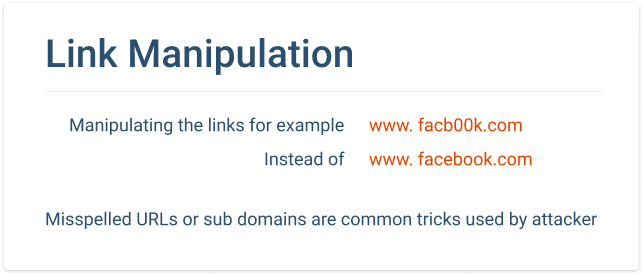
Photo by MSP360 on msp360.com
Malware Delivery
Embedding ransomware, keyloggers, or spyware in attachments or links.
Credential Harvesting
Creating fake login pages that mimic legitimate sites to steal usernames and passwords.

Photo by Microsoft on microsoft.com
Social Engineering
Exploiting trust by referencing real-world events, personal details, or company-specific jargon gathered from social media or data breaches.
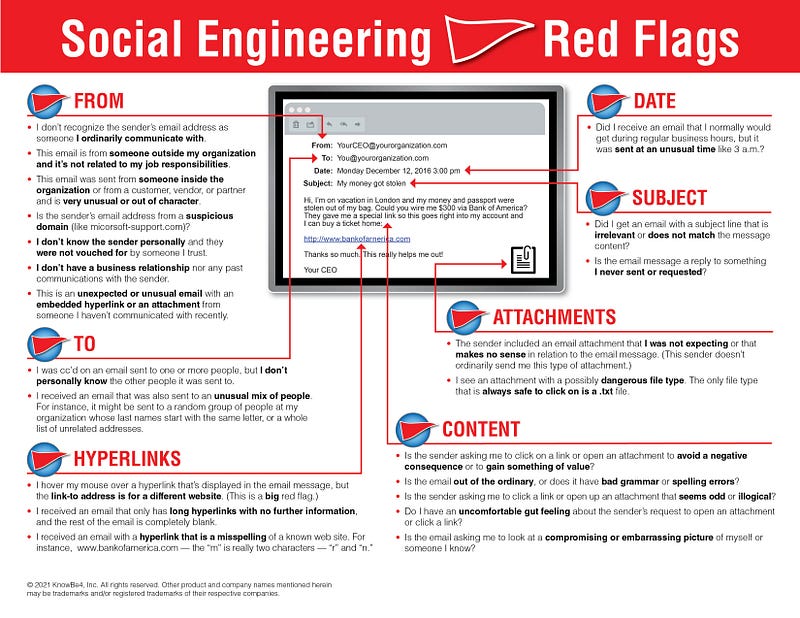
Photo by Knowbe4 on info.knowbe4.com
AI-Powered Phishing
Using machine learning to craft convincing emails or mimic a target’s writing style.
Anti-phishing Measures
Combating phishing requires a multi-layered approach involving awareness, policies, and technology.
For Employees
Verify the Source: Always double-check email addresses, phone numbers, and URLs. Hover over links (without clicking) to see the real destination.
Be Skeptical: Question unexpected requests, especially those demanding urgency or sensitive information. When in doubt, contact the sender through a known channel.
Avoid Attachments and Links: Don’t open unsolicited attachments or click links unless you’re certain of their legitimacy.
Use Strong, Unique Passwords: Combine this with multi-factor authentication (MFA) to limit damage if credentials are stolen.
Report Suspicious Activity: Notify your IT or security team immediately if something seems off.
For Organizations
Employee Training: Conduct regular phishing simulations and awareness programs to teach staff how to spot and respond to attacks.
Email Filtering: Deploy advanced spam filters and domain authentication protocols (e.g., DMARC, SPF, DKIM) to block spoofed emails.
Endpoint Security: Use antivirus software and endpoint detection tools to catch malware delivered via phishing.
Incident Response Plan: Establish clear procedures for reporting and mitigating phishing incidents.
MFA Enforcement: Require MFA across all systems to reduce the impact of stolen credentials.
Technical Approach as a SOC Analyst:
For SOC analysts, phishing is a daily battle requiring proactive monitoring, rapid response, and forensic skills. Here’s a technical roadmap to combat phishing effectively:
1. Threat Detection
SIEM Integration: Use Security Information and Event Management (SIEM) tools like Splunk or QRadar to aggregate logs from email gateways, firewalls, and endpoints. Set up rules to flag suspicious patterns (e.g., mass emails from unknown domains).
Email Gateway Analysis: Monitor email traffic for spoofed headers, malicious attachments, or unusual link destinations using tools like Proofpoint or Mimecast.
Network Monitoring: Leverage Intrusion Detection Systems (IDS) like Snort or Suricata to detect traffic to known phishing domains.
2. Investigation
Analyze Headers: Examine email headers to trace the true origin of a phishing attempt, identifying spoofed domains or compromised accounts.
Sandboxing: Detonate suspicious attachments or URLs in a virtualized sandbox (e.g., Cuckoo or Any.Run) to analyze their behavior safely.
User Behavior Analytics (UBA): Use tools like Exabeam or Darktrace to spot anomalies, such as an employee suddenly downloading files after clicking a link.
3. Response
Containment: Block malicious IPs or domains at the firewall, quarantine affected emails, and disable compromised accounts.
User Notification: Alert employees about the campaign and provide guidance (e.g., “Do not click links in emails claiming to be from HR”).
Forensics: Preserve evidence like email headers, payloads, and logs for analysis and potential law enforcement reporting.
4. Prevention
Threat Intelligence: Subscribe to feeds (e.g., Cisco Talos, Recorded Future) to stay ahead of emerging phishing trends and update defenses accordingly.
Patch Management: Ensure systems are updated to prevent exploitation of vulnerabilities often paired with phishing attacks.
Simulation: Run controlled phishing exercises to test employee resilience and refine detection rules.
Tools for SOC Analysts
Wireshark: For packet-level analysis of phishing-related traffic.
VirusTotal: To check URLs, files, and IPs against known threats.
PhishTank: A database of verified phishing sites for cross-referencing.
YARA Rules: Custom signatures to detect phishing payloads in memory or files.
Stay informed, stay cautious, and keep phishing at bay.
Additional Resources
https://www.itgovernance.co.uk/blog/5-ways-to-detect-a-phishing-email
https://cheapsslsecurity.com/blog/10-phishing-email-examples-you-need-to-see/
Please check out https://github.com/l00pinfinity/blog-stories. It contains my blog posts online, do you have any suggestions? A correction, perhaps? Make a pull request on Github or open an issue.
Thanks for reading and stay tuned!!!